记两道Mobile题的Writeup
潜心 2022-5-26 MobileISCC2022
第一次接触Mobile题,记录一下
# 控车密码忘记了
题目:CICV智能网联汽车漏洞挖掘赛 - 线上CTF夺旗赛
需要满足:输入的内容的每个字符等于versionName对应字符与versionCode异或的结果,同时长度要和versionName相同
其中,versionName="210B4BA5D254ACD3",versionCode=10
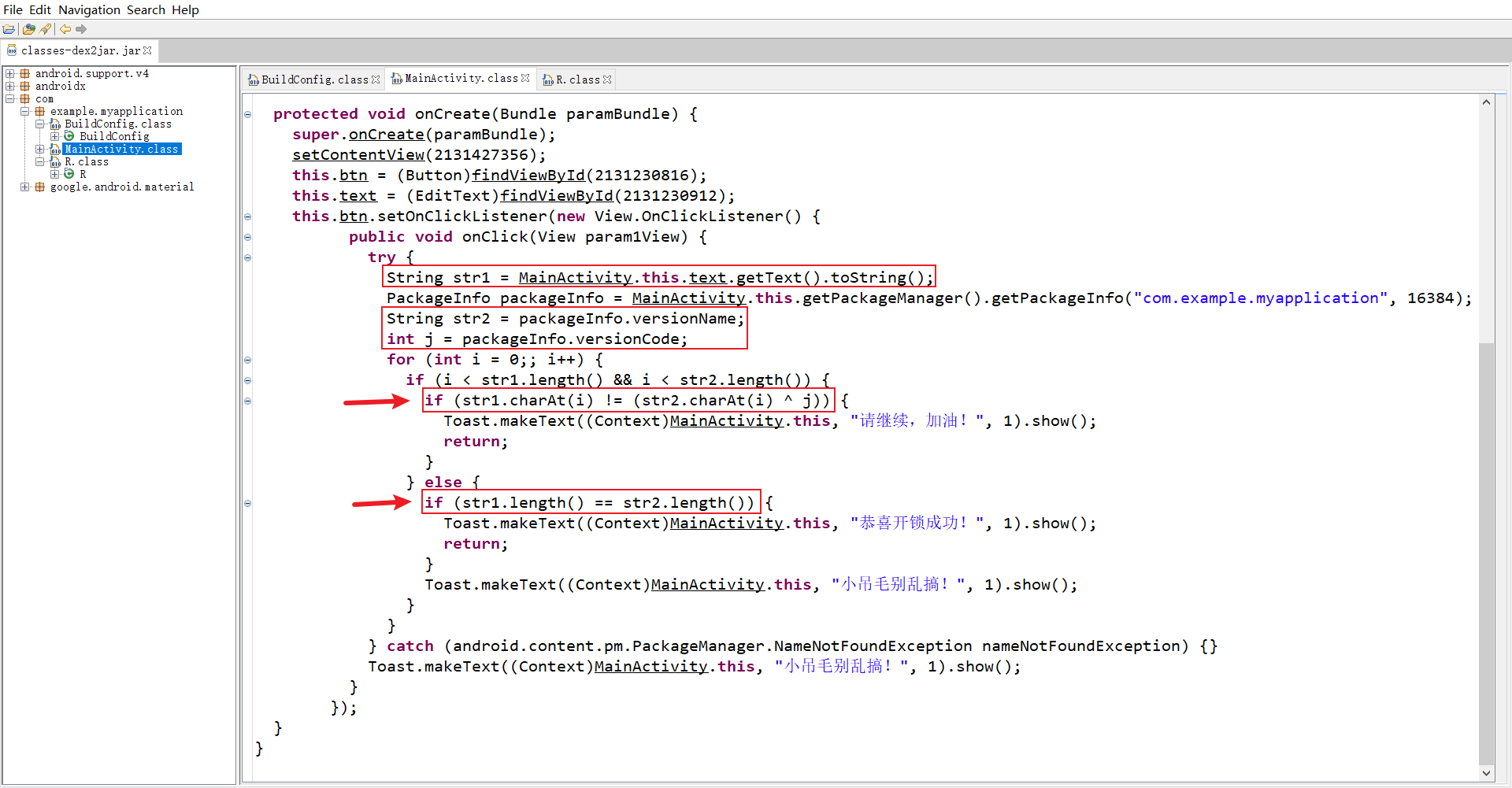
versionName="210B4BA5D254ACD3"
versionCode=10
for i in versionName:
print(chr(ord(i)^versionCode), end="")
# 8;:H>HK?N8?>KIN9
1
2
3
4
5
6
7
2
3
4
5
6
7
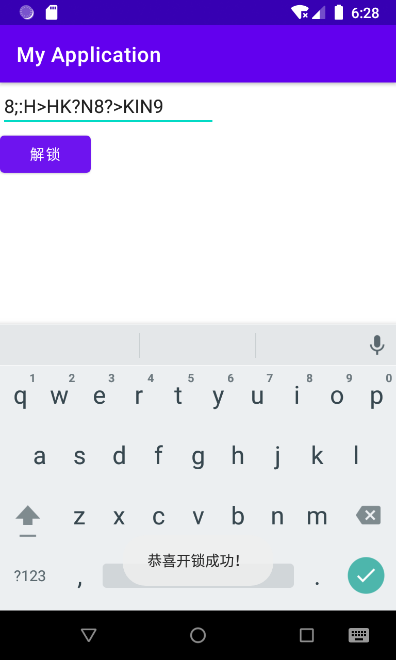
flag为密码的md5,所以flag为
flag{de1e7c178845a8d407b1b8060ffd2b16}
1
# MobileA
题目:ISCC2022 个人挑战赛(第19届信息安全与对抗技术竞赛)
flag由两部分组成:
# 第一部分
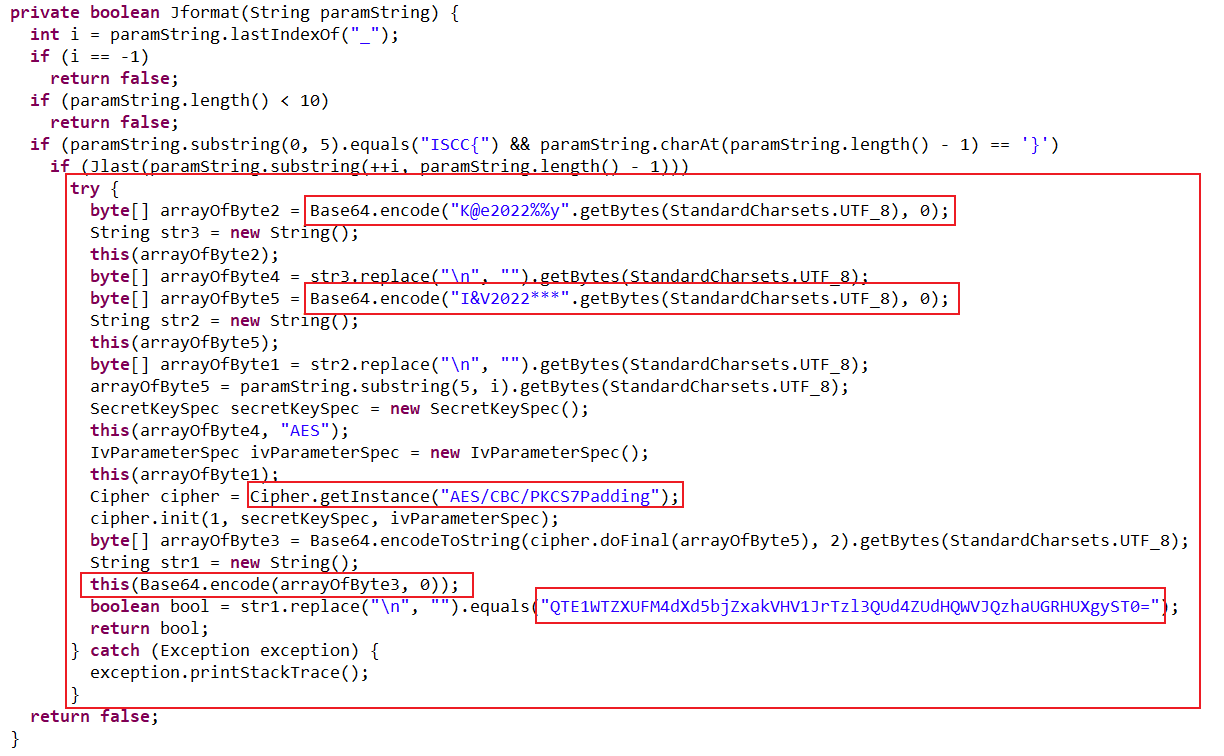
密钥
K@e2022%%y 进行base64编码1偏移
I&V2022*** 进行base64编码1模式
AES/CBC/PKCS7Padding1运行结果
QTE1WTZXUFM4dXd5bjZxakVHV1JrTzl3QUd4ZUdHQWVJQzhaUGRHUXgyST0= 进行base64解码1
在线AES加密解密、AES在线加密解密、AES encryption and decryption--查错网 (chacuo.net) (opens new window)
Java 中的加密算法: AES - 知乎 (zhihu.com) (opens new window)
package top.mrzry.mobile;
import android.os.Build;
import android.support.annotation.RequiresApi;
import android.support.v7.app.AppCompatActivity;
import android.os.Bundle;
import android.util.Log;
import java.security.InvalidAlgorithmParameterException;
import java.security.InvalidKeyException;
import java.security.NoSuchAlgorithmException;
import java.util.Base64;
import javax.crypto.BadPaddingException;
import javax.crypto.Cipher;
import javax.crypto.IllegalBlockSizeException;
import javax.crypto.NoSuchPaddingException;
import javax.crypto.spec.IvParameterSpec;
import javax.crypto.spec.SecretKeySpec;
public class MainActivity extends AppCompatActivity {
@RequiresApi(api = Build.VERSION_CODES.O)
@Override
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
setContentView(R.layout.activity_main);
byte[] flag1 = new byte[0];
byte[] ciphertext1 = Base64.getDecoder().decode("QTE1WTZXUFM4dXd5bjZxakVHV1JrTzl3QUd4ZUdHQWVJQzhaUGRHUXgyST0=");
byte[] key = Base64.getEncoder().encode("K@e2022%%y".getBytes());
byte[] iv = Base64.getEncoder().encode("I&V2022***".getBytes());
try {
Cipher cipher = Cipher.getInstance("AES/CBC/PKCS7Padding");
cipher.init(Cipher.DECRYPT_MODE, new SecretKeySpec(key, "AES"), new IvParameterSpec(iv));
flag1 = cipher.doFinal(Base64.getDecoder().decode(ciphertext1));
} catch (NoSuchPaddingException | InvalidAlgorithmParameterException | InvalidKeyException | NoSuchAlgorithmException | IllegalBlockSizeException | BadPaddingException e) {
e.printStackTrace();
}
Log.i("flag1", new String(flag1)); // sadasfsdASDWFSASAFfasf_
}
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
# 第二部分
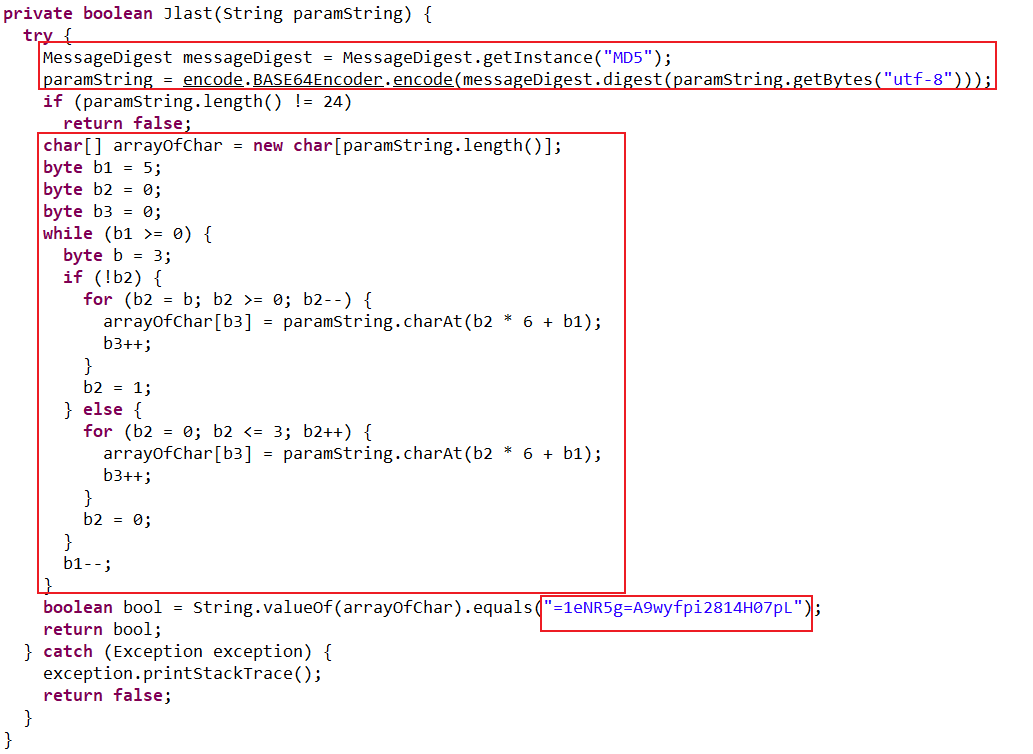
先md5再base64编码,之后进行加密,先得出加密前的字符串
public class Hello {
public static void main(String[] args) {
String old_table = "abcdefghijklmnopqrstuvwx";
String new_table = Jlast(old_table);
System.out.println(new_table); // xrlfekqwvpjdcioutnhbagms
String paramString = "=1eNR5g=A9wyfpi2814H07pL";
char[] flag = new char[paramString.length()];
for (int i = 0; i < paramString.length(); i++) {
int index = new_table.indexOf(old_table.charAt(i));
flag[i] = paramString.charAt(index);
}
System.out.println(flag); // 0HfyRN74pw5ep1i9g1L82A==
}
public static String Jlast(String paramString) {
char[] arrayOfChar = new char[paramString.length()];
byte b1 = 5;
byte b2 = 0;
byte b3 = 0;
while (b1 >= 0) {
byte b = 3;
if (b2 == 0) {
for (b2 = b; b2 >= 0; b2--) {
arrayOfChar[b3] = paramString.charAt(b2 * 6 + b1);
b3++;
}
b2 = 1;
} else {
for (b2 = 0; b2 <= 3; b2++) {
arrayOfChar[b3] = paramString.charAt(b2 * 6 + b1);
b3++;
}
b2 = 0;
}
b1--;
}
return String.valueOf(arrayOfChar);
}
}
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
爆破得到flag的第二部分
import base64
import hashlib
import string
flag = "0HfyRN74pw5ep1i9g1L82A=="
flag = base64.b64decode(flag)
H = ''
for i in flag:
H += hex(i).replace('0x', '').zfill(2)
print(H)
table = string.ascii_letters + string.digits
for s1 in table:
for s2 in table:
for s3 in table:
ss = s1 + s2 + s3
h = hashlib.md5(ss.encode()).hexdigest()
if h == H:
print(ss)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
d077f244def8a70e5ea758bd8352fcd8
cat
1
2
2
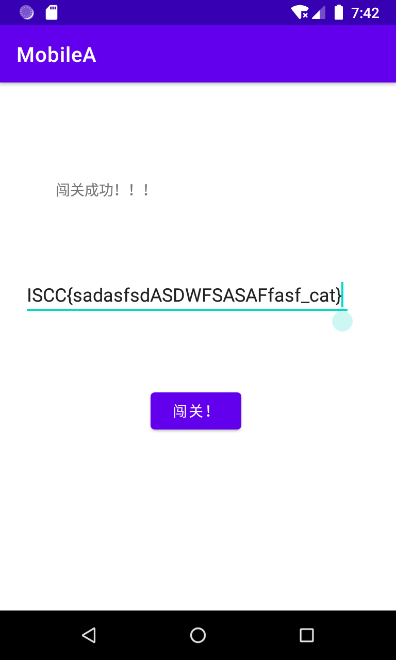
ISCC{sadasfsdASDWFSASAFfasf_cat}
1
